Create a KMS configuration
Encryption at rest uses a master key to encrypt and decrypt universe keys. The master key details are stored in YugabyteDB Anywhere in key management service (KMS) configurations. You enable encryption at rest for a universe by assigning the universe a KMS configuration. The master key designated in the configuration is then used for generating the universe keys used for encrypting the universe data.
Encryption at rest in YugabyteDB Anywhere supports the use of Microsoft Azure Key Vault.
Conceptually, Azure Key Vault consists of a key vault containing one or more keys, with each key capable of having multiple versions.
If you are planning to use an existing cryptographic key with the same name, it must meet the following criteria:
- The primary key version should be in the Enabled state.
- The activation date should either be disabled or set to a date before the KMS configuration creation.
- The expiration date should be disabled.
- Permitted operations should have at least WRAP_KEY and UNWRAP_KEY.
- The key rotation policy should not be defined in order to avoid automatic rotation.
Note that YugabyteDB Anywhere does not manage the key vault and deleting the KMS configuration does not delete the key vault, master key, or key versions on Azure Key Vault.
Prerequisites
Before defining a KMS configuration with YugabyteDB Anywhere, you need to create a key vault through the Azure portal. The following settings are required:
- Set the vault permission model as Vault access policy.
- Add the application to the key vault access policies with the minimum key management operations permissions of Get and Create (unless you are pre-creating the key), as well as cryptographic operations permissions of Unwrap Key and Wrap Key.
Create a KMS configuration
You can create a KMS configuration that uses Azure Key Vault, as follows:
-
Navigate to Integrations > Security > Encryption At Rest to access the list of existing configurations.
-
Click Create New Config.
-
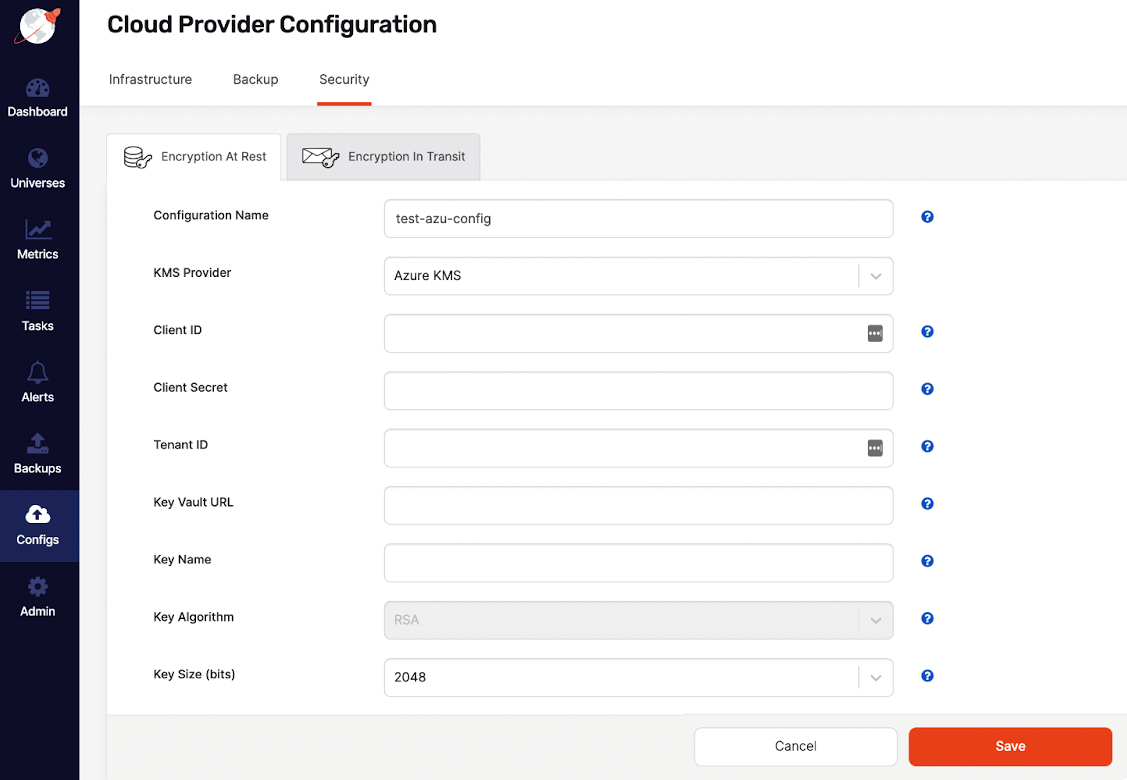
Enter the following configuration details in the form:
- Configuration Name — Enter a meaningful name for your configuration.
- KMS Provider — Select Azure KMS.
- Client ID — Enter the Azure Active Directory (AD) application client ID.
- Client Secret — Enter the Azure AD application client secret.
- Tenant ID — Enter the Azure AD application tenant ID.
- Key Vault URL — Enter the key vault URI, as per your Azure portal Key Vault definition that should allow you to use the preceding three credentials to gain access to an application created in the Azure AD.
- Key Name — Enter the name of the master key. If a master key with the same name already exists in the key vault, the settings are validated and the existing key is used; otherwise, a new key is created automatically.
- Key Algorithm — The algorithm for the master key. Currently, only the RSA algorithm is supported.
- Key Size — Select the size of the master key, in bits. Supported values are 2048 (default), 3072, and 4096.
-
Click Save.
Your new configuration should appear in the list of configurations.
-
Optionally, to confirm that the information is correct, click Show details. Note that sensitive configuration values are displayed partially masked.
Modify a KMS configuration
You can modify an existing KMS configuration as follows:
-
Navigate to Integrations > Security > Encryption At Rest to open a list of existing configurations.
-
Find the configuration you want to modify and click its corresponding Actions > Edit Configuration.
-
Provide new values for the Vault Address and Secret Token fields.
-
Click Save.
-
Optionally, to confirm that the information is correct, click Show details or Actions > Details.
Delete a KMS configuration
Note
Without a KMS configuration, you would longer be able to decrypt universe keys that were encrypted using the master key in the KMS configuration. Even after a key is rotated out of service, it may still be needed to decrypt data in backups and snapshots that were created while it was active. For this reason, you can only delete a KMS configuration if it has never been used by any universes.To delete a KMS configuration, click its corresponding Actions > Delete Configuration.