Add certificates
Instead of using YugabyteDB Anywhere-provided certificates, you can use your own self-signed certificates that you upload to YugabyteDB Anywhere.
Prerequisites
The certificates must meet the following criteria:
- Be in the
.crtformat and the private key must be in the.pemformat, with both of these artifacts available for upload.
YugabyteDB Anywhere produces the node (leaf) certificates from the uploaded certificates and copies the certificate chain, leaf certificate, and private key to the nodes in the cluster.
Convert certificates and keys from PKCS12 to PEM format
If your certificates and keys are stored in the PKCS12 format, you can convert them to the PEM format using OpenSSL.
Start by extracting the certificate via the following command:
openssl pkcs12 -in cert-archive.pfx -out cert.pem -clcerts -nokeys
To extract the key and write it to the PEM file unencrypted, execute the following command:
openssl pkcs12 -in cert-archive.pfx -out key.pem -nocerts -nodes
If the key is protected by a passphrase in the PKCS12 archive, you are prompted for the passphrase.
Add self-signed certificates
To add self-signed certificates to YugabyteDB Anywhere:
-
Navigate to Integrations > Security > Encryption in Transit.
-
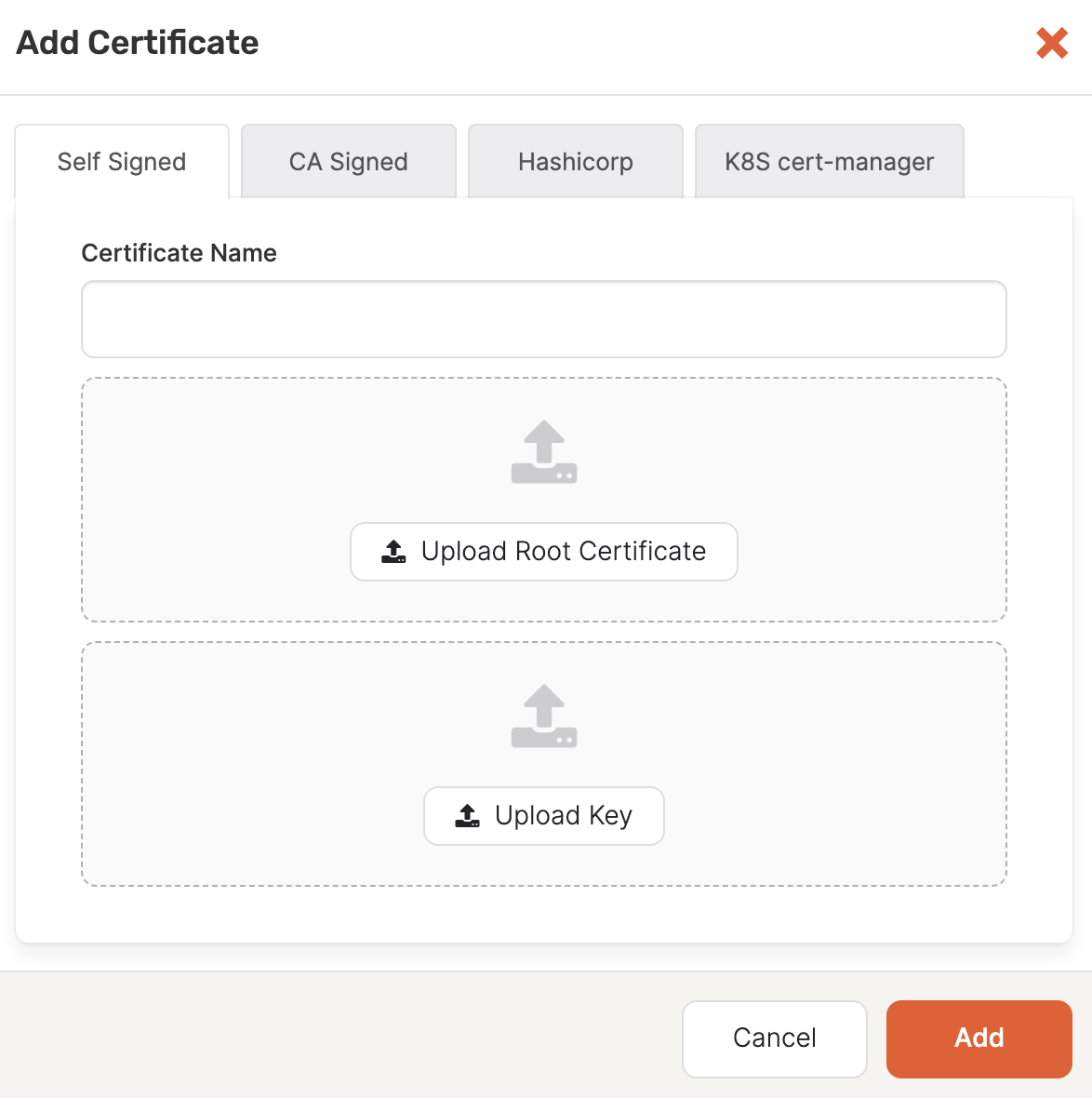
Click Add Certificate to open the Add Certificate dialog.
-
Select Self Signed.
-
In the Certificate Name field, enter a meaningful name for your certificate.
-
Click Upload Root Certificate, then browse to the root certificate file (
<file-name>.crt) and upload it. -
Click Upload Key, then browse to the root certificate file (
<file-name>.key) and upload it. -
In the Expiration Date field, specify the expiration date of the root certificate. To find this information, execute the
openssl x509 -in <root-crt-file-path> -text -nooutcommand and note the Validity Not After date. -
Click Add to make the certificate available.
Validate certificates
When configuring and using certificates, SSL issues may occasionally arise. You can validate your certificates and keys as follows:
-
Verify that the CA CRT and CA private key match by executing the following commands:
openssl rsa -noout -modulus -in ca.key | openssl md5 openssl x509 -noout -modulus -in ca.crt | openssl md5 \# outputs should match -
Verify that the CA CRT is actually a certificate authority by executing the following command:
openssl x509 -text -noout -in ca.crt \# Look for fields X509v3 Basic Constraints: CA:TRUE -
Verify that certificates and keys are in PEM format (as opposed to the DER or other format). If these artifacts are not in the PEM format and you require assistance with converting them or identifying the format, consult Converting certificates.
-
Ensure that the private key does not have a passphrase associated with it. For information on how to identify this condition, see Decrypt an encrypted SSL RSA private key.